yoast seo premium
Drive more traffic to your website
Automate technical SEO and make optimizing content a breeze with the most popular WordPress SEO plugin.
Compare Yoast SEO Premium to the free version
What does Yoast SEO Premium do?
Yoast SEO Premium includes all the features of the free version, plus many additional benefits. After installation, Yoast SEO Premium simplifies site optimization, boosts organic traffic, and saves you time on SEO tasks.
Watch how Yoast SEO Premium helps you rank higher
Unlock the power of Yoast SEO Premium! Watch this 2-minute video to see how Yoast SEO Premium helps you rank higher by making your site irresistible for both users and search engines.

I have been using Yoast SEO Premium on my websites and client websites for many years. I love how it points out orphaned content and suggests linking to specific articles and pages on my website. I also like the automatic redirect when I delete or change the permalink for blog posts or pages. Very helpful and saves a great deal of time!”
Dotty Scott – Premium Websites, Inc
Get ahead of the game with Yoast SEO!
Yoast SEO Premium
- All Yoast SEO Premium features
- Full access to the Yoast SEO Academy
- Yoast Local SEO
- Yoast News SEO
- Yoast Video SEO
- One seat access to Yoast SEO Google Docs add-on
Yoast SEO
- Only Yoast SEO basic features
Premium features
Yoast SEO Premium in detail
Yoast SEO Premium helps you grow organic traffic to your site and gives you access to all these exclusive features.
Reach a wider audience with the same content
Creating captivating content is only half the battle; the next challenge is getting people to see it. Yoast SEO Premium is your secret weapon!
Optimize for up to 5 keywords per page
Why limit yourself to a single keyword when you can cast a wider net? With the ability to target up to 5 keywords, you’re speaking the language of your diverse audience. This strategic move allows you to appear in a broader range of search results, capturing the attention it deserves.
Effortlessly write content your audience loves
Create engaging, natural content that captivates your readers without stressing over repetitive keywords. The advanced analysis understands keyword variations, including word forms, plurals, and synonyms, so you can focus on crafting impactful content that resonates with your audience.
Speed up and automate day-to-day SEO tasks with AI
Yoast SEO Premium means less manual work and more consistent, high-quality content all throughout.
Use generative AI to create SEO titles & meta descriptions
Why spend hours crafting perfect titles and descriptions when you can automate it? Yoast SEO’s AI feature empowers you to create effective, engaging titles and meta descriptions at the click of a button. It combines advanced AI technology with Yoast’s linguistic expertise, saving you time and kickstarting your SEO processes.
Get AI-powered suggestions to optimize your content
Optimizing content for SEO is tedious, but it doesn’t have to be that way. Use Yoast SEO’s AI feature and get suggestions to improve your content at a click. It helps you ensure your content is search engine-friendly while making your life easier. This feature is in beta.
Get help while working on your SEO
With Yoast SEO Premium, you’re never alone in your SEO journey.
24/7 support
Whenever you hit a roadblock, expert assistance is just a click away. Get answers, advice, and guidance for Yoast SEO on demand.
Improve your SEO skills with the SEO Academy
Learn vital SEO skills in the Yoast SEO Academy, the online learning environment. Take your pick of the SEO-related, on-demand courses ranging from beginner level to advanced level.

Make fewer SEO mistakes
Experience fewer hiccups on your SEO journey with Yoast SEO Premium. Navigate with ease and reduce common SEO errors.
No more dead links or 404 errors
Enhance user experience by eliminating dead ends. The redirect manager highlights broken links, helping you create seamless navigation even when content shifts.
Freshen up outdated content
Quickly identify and fix unlinked pages, also known as “orphaned content”. This helps you stay relevant and helpful for users and improves your internal linking structure.
Easily create content that ranks
Frustrated by content that doesn’t rank? Let Yoast SEO Premium be your guide.
Unlock the Premium SEO analysis
With Yoast SEO Premium, you get an extra thorough analysis, including extra SEO checks, related keywords & synonyms recognition.
Internal linking tools
You get smart suggestions for links to other pages as you write. Google loves internal links and will reward you with a better ranking. Simply follow the guided internal linking workflow.
* Available in English, Dutch, German, French, Russian, Italian, Spanish, Swedish, Portuguese, Polish, Arabic, Hebrew, Hungarian, Norwegian, Turkish, Norwegian, Slovak, Czech, Indonesian, Greek, and Japanese

Get more clicks on your social posts
Social media appearance preview
Make a lasting first impression with the social appearance preview. Sample and tweak content for social platforms, ensuring it’s eye-catching, share-worthy, and generating clicks to your site.
Increase visibility in local searches
Local SEO is now included with Yoast SEO Premium!
Easily boost your visibility in local search queries with automatic structured data for business details and hassle-free technical setup. Yoast Local SEO helps you manage multiple locations smoothly and embed Google Maps for a seamless visitor experience.
Improve your video’s performance and findability
Video SEO is now included with Yoast SEO Premium!
Make your videos easier to find for both your visitors and search engines with automatic structured data and video sitemaps. The plugin also helps your videos load fast, look great on any device, and stand out with custom thumbnail, helping you attract more views without extra effort.

Optimize your site for Google News
News SEO is now included with Yoast SEO Premium!
If you’re a news publisher, your aim is that top result for every news story you publish. With Yoast News SEO by your side, you always get technical SEO best practices without having to worry a thing. Get your news noticed with real-time XML News sitemaps and automatic schema markup. Control which articles get indexed and add extra details like stock tickers.

Yoast SEO Premium helped me realize how to better understand the rules of optimized content and help boost visibility rankings! I highly recommend it to everyone, who wishes to get high search engine results.
Koveos Konstantinos – Athens Coast Hotel
Frequently asked questions about Yoast SEO Premium
When you buy Yoast SEO Premium, we’ll take you through a clear installation flow.
If you’ve already bought Yoast SEO Premium, you can find clear step-by-step instructions for installing the plugin in the Yoast Help Center!
If you’d like some extra help, just contact our expert support team at support@yoast.com. They are available 24/7 to guide you through the installation process!
All plugin settings will be automatically migrated to Yoast SEO Premium for you. So you keep all the work you’ve already put into your free plugin.
1 Yoast SEO Premium subscription can be used on 1 website or domain.
You can use Yoast SEO Premium on multiple websites by purchasing more than one subscription. You can choose how many sites you need it for on the check-out page.
And of course, you get a discount.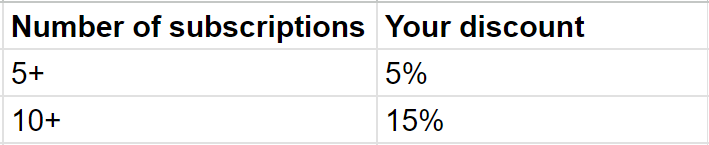
Absolutely! That’s easy to do. Just remove the subscription on one site and then add it to another site.
We have a clear step-by-step guide in the Yoast Help Center to help you out.
Yes, you can! Yoast SEO Premium is available in English, Spanish, German, Dutch, French, Italian, Portuguese, Russian, Polish, Swedish, Hungarian, Indonesian, Arabic, Hebrew, Norwegian, Turkish, and Czech.
Yes! You can use your Yoast SEO Premium on your staging site.
Simply add both your live and staging site in MyYoast and transfer subscription(s) between the live and development site. We have a clear step-by-step guide in the Yoast Help Center to help you out.